Attackers Breach Microsoft 365 Using Fake OAuth Apps — Here’s What You Need to Know
⚠️ Attackers Breach Microsoft 365 Using Fake OAuth Apps — Here’s What You Need to Know Cybercriminals have evolved once again. A newly uncovered attack wave is leveraging fake[…]

Kick off your Azure Automation Journey!
Automate Your Azure Like a Pro: Create an Automation Account + Scheduled Runbook Automation in Azure isn’t just a luxury — it’s a superpower. Whether you’re managing resources, rotating[…]

Step-by-Step – Create VNet Peering in Azure (Securely)
🔄 What Is VNet Peering? VNet Peering enables private, high-speed communication between two virtual networks (VNets) in Azure—across the same region or even globally. It’s like running a fiber[…]

Step-by-Step – Create a Secure Azure VNet
Step-by-Step – Create a Secure Azure VNet 🧱 What is a VNet? A Virtual Network (VNet) is Azure’s foundational building block for securely connecting your VMs, services, and workloads.[…]
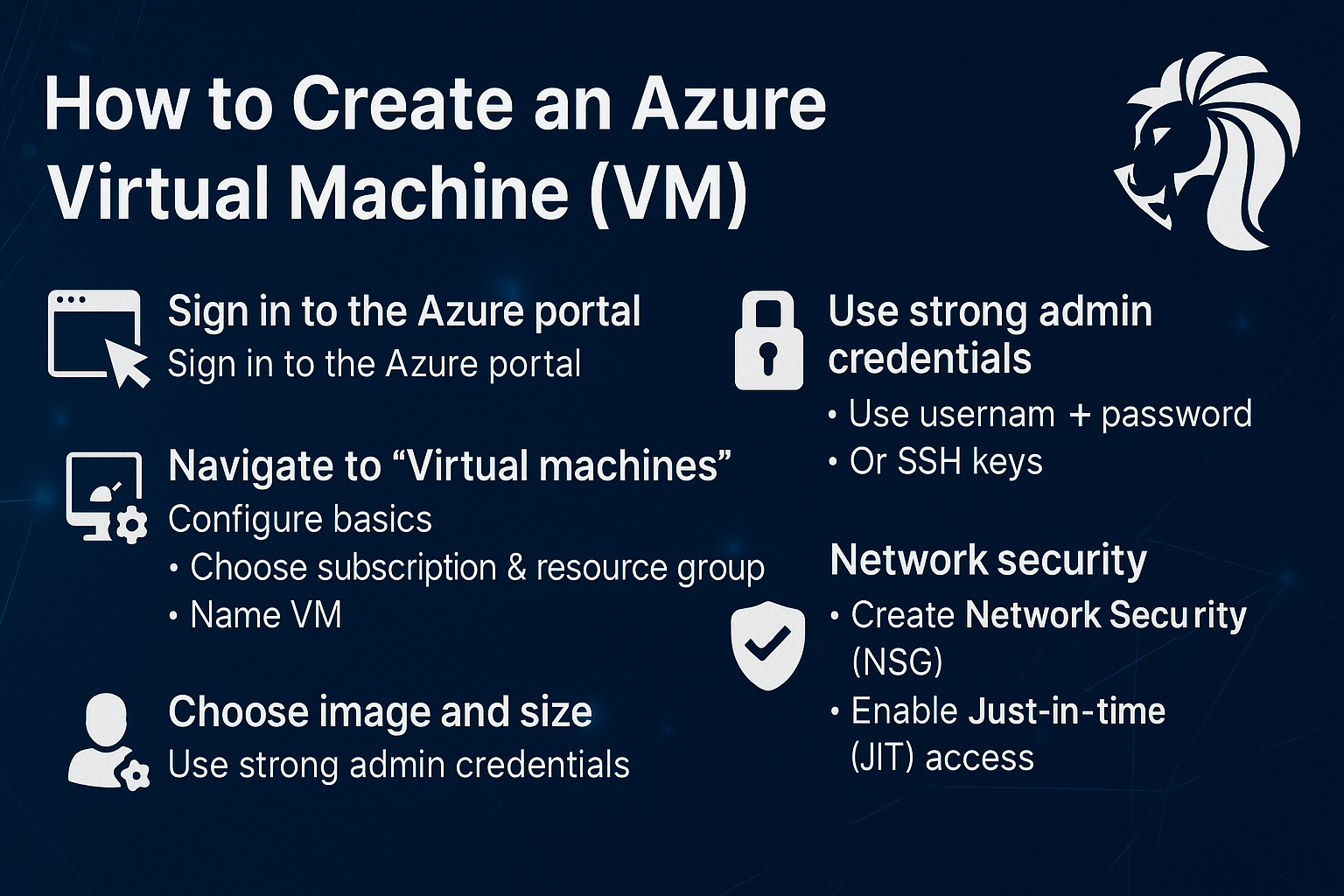
How to Create a Virtual Machine in Microsoft Azure
Deploying a Virtual Machine (VM) in Azure is one of the first tasks in cloud adoption—and it can be done in minutes. But what sets professionals apart is how[…]

Hackers Use Microsoft Teams to Spread Matanbuchus 3.0 Malware Loader
Hackers Use Microsoft Teams to Spread Matanbuchus 3.0 Malware Loader Threat researchers have uncovered a new wave of cyberattacks using Microsoft Teams as a delivery vector for Matanbuchus 3.0,[…]
Microsoft Issues Emergency Update to Resolve Azure VM Startup Failure (KB5064489)
⚠️ Microsoft Issues Emergency Update to Resolve Azure VM Startup Failure (KB5064489) Microsoft has published an urgent out-of-band update—KB5064489—to address a serious issue affecting Azure virtual machines. The problem,[…]

Microsoft Patches 130 Security Flaws—Critical Issues Found in SQL Server and SPNEGO
🔒 Microsoft Patches 130 Security Flaws—Critical Issues Found in SQL Server and SPNEGO In July 2025, Microsoft released security updates addressing 130 vulnerabilities, including 10 critical issues impacting key[…]
