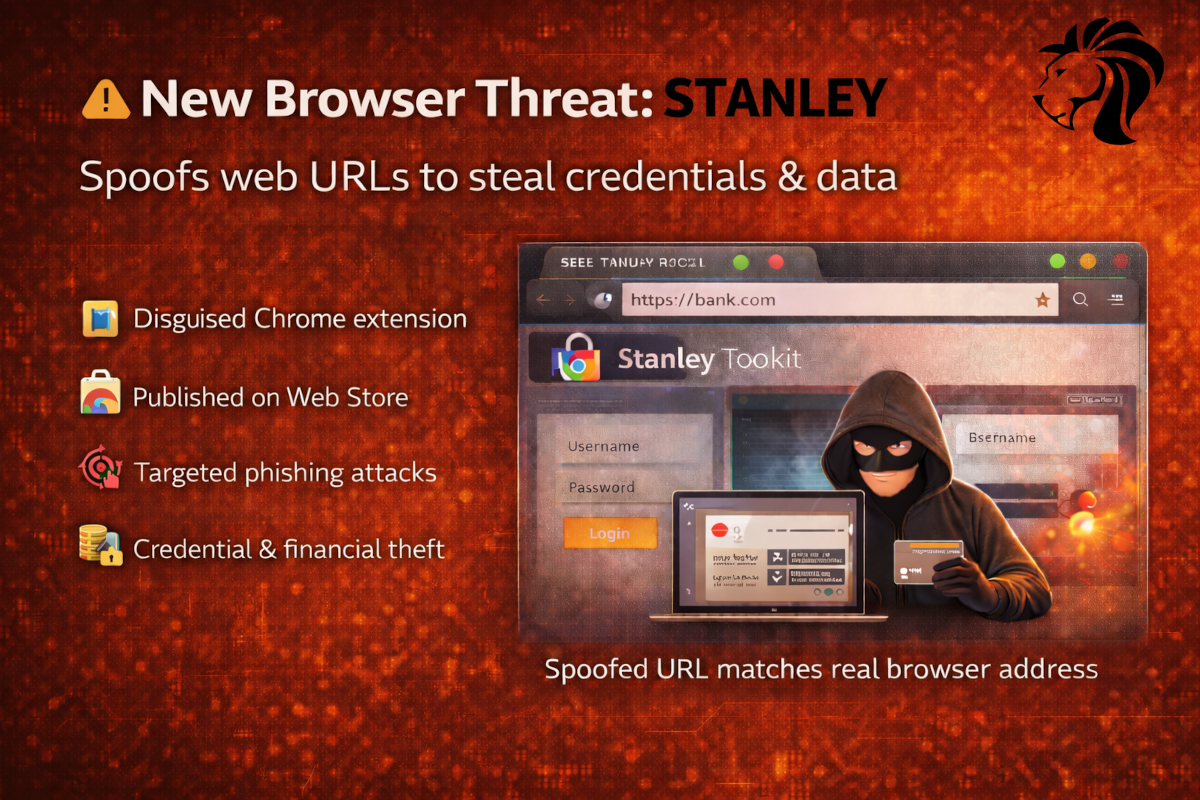
Browser Attacks Are Evolving — “Stanley” Sets a New Benchmark
Browser Attacks Are Evolving — “Stanley” Sets a New Benchmark Discovered in January 2026, a new malware-as-a-service toolkit called Stanley highlights the increasing sophistication of browser-based threats. 💰 Sold[…]

EU moves to harden telecom and ICT supply chains against cyber threats
EU moves to harden telecom and ICT supply chains against cyber threats 🏛️ The European Commission has proposed a new cybersecurity legislative package aimed at protecting telecommunications networks and[…]
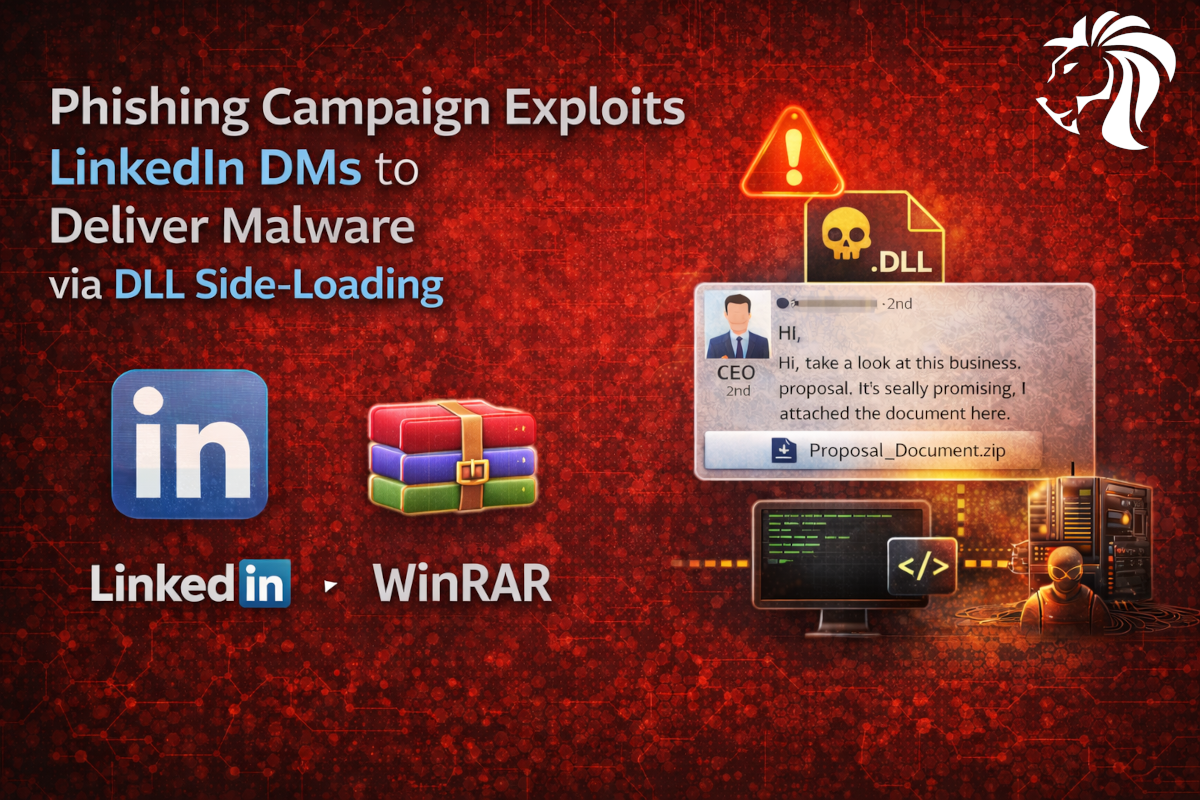
Phishing Campaign Exploits LinkedIn DMs to Deliver Malware via DLL Side-Loading
Phishing Campaign Exploits LinkedIn DMs to Deliver Malware via DLL Side-Loading Cybersecurity researchers have uncovered a new phishing campaign abusing social media private messages, particularly LinkedIn, to distribute malware[…]

ChatGPT Health: A New Era for AI Health Advice — With Real Security Risks
ChatGPT Health: A New Era for AI Health Advice — With Real Security Risks 🩺🤖 OpenAI has announced ChatGPT Health, a dedicated consumer AI experience designed to help users[…]

Ingram Micro confirms ransomware-linked data breach impacting over 42,000 individuals
Ingram Micro confirms ransomware-linked data breach impacting over 42,000 individuals 🏢 Ingram Micro, one of the world’s largest B2B technology distributors, has confirmed that a ransomware attack in July[…]

Active Exploitation: Critical WordPress Plugin Vulnerability (CVSS 10.0)
Active Exploitation: Critical WordPress Plugin Vulnerability (CVSS 10.0) Patchstack has confirmed the active exploitation of a maximum-severity vulnerability in the Modular DS WordPress plugin, affecting over 40,000 sites. 🔓 CVE-2026-23550 allows unauthenticated privilege escalation, enabling[…]

Privilege Escalation Risks Found in Google Vertex AI Defaults
Privilege Escalation Risks Found in Google Vertex AI Defaults Security researchers from XM Cyber have disclosed that default configurations in Google Vertex AI can allow low-privileged users to escalate[…]

Cisco Confirms Active Exploitation of Critical Zero-Day in Secure Email Appliances
Cisco Confirms Active Exploitation of Critical Zero-Day in Secure Email Appliances Cisco has confirmed active exploitation of a critical zero-day remote code execution vulnerability affecting Cisco Secure Email Gateway[…]
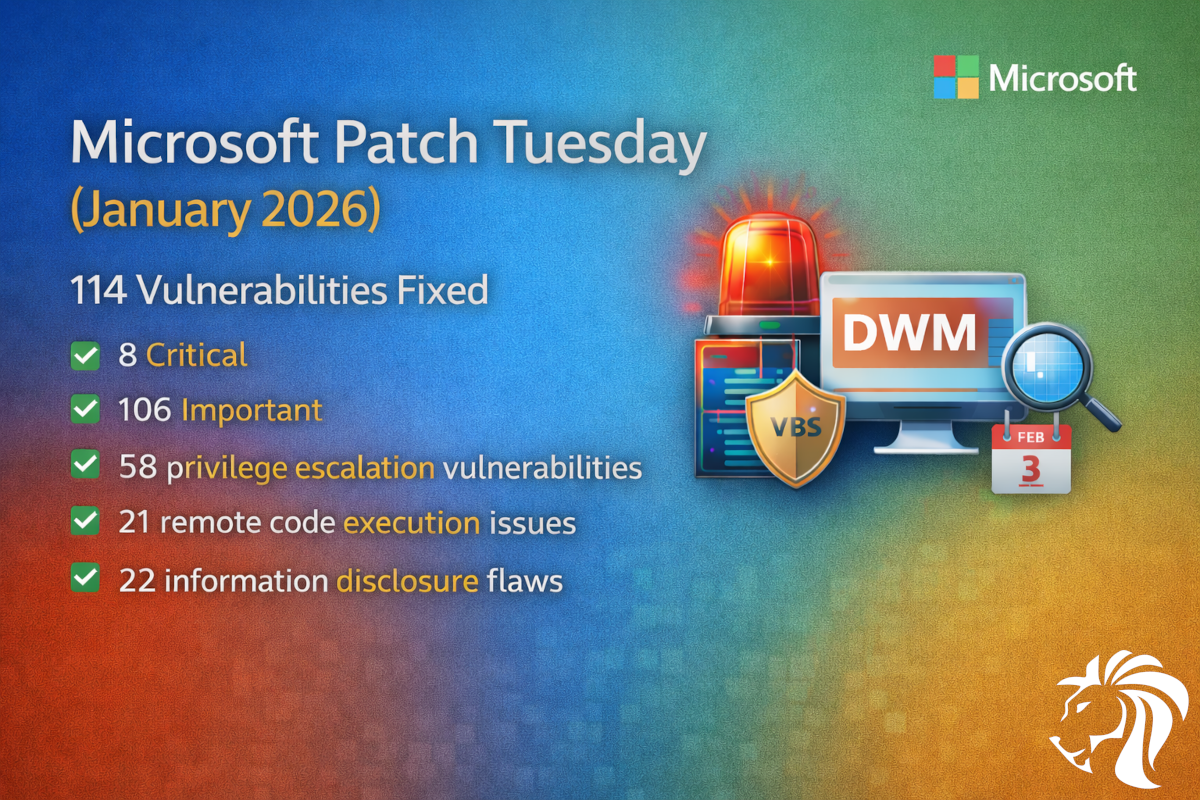
Microsoft Patch Tuesday (January 2026): 114 Vulnerabilities Fixed
Microsoft Patch Tuesday (January 2026): 114 Vulnerabilities Fixed Microsoft has released its first security update of 2026, addressing 114 vulnerabilities, including one flaw actively exploited in the wild. 🔐[…]

Azure Monitor – Overview, Components & Configuration Options
Azure Monitor – Overview, Components & Configuration Options 1. What is Azure Monitor? Azure Monitor is a centralized observability platform in Microsoft Azure that collects, analyzes, and acts on[…]
