
Zoom & Xerox Issue Critical Patches Fixing Privilege Escalation and RCE Vulnerabilities
Zoom & Xerox Issue Critical Patches Fixing Privilege Escalation and RCE Vulnerabilities Two major software vendors, Zoom and Xerox, have released critical security updates that address vulnerabilities potentially exploitable by attackers to gain[…]

Microsoft August 2025 Patch Tuesday: 107 Flaws Fixed, Including a Windows Kerberos Zero-Day
Microsoft August 2025 Patch Tuesday: 107 Flaws Fixed, Including a Windows Kerberos Zero-Day On August 12, 2025, Microsoft released its monthly Patch Tuesday updates, addressing 107 vulnerabilities across its[…]

Air France & KLM Report Data Breach
Air France and KLM have confirmed a data breach involving their customer service platform, resulting in the theft of personal information such as names, email addresses, phone numbers, loyalty[…]

Automatyzuj Azure jak profesjonalista: Tworzenie Automation Account + zaplanowanego Runbooka
Automatyzuj Azure jak profesjonalista: Tworzenie Automation Account + zaplanowanego Runbooka Automatyzacja w Azure to nie luksus — to supermoc!Niezależnie od tego, czy zarządzasz zasobami, rotujesz sekrety, generujesz raporty, czy[…]

Pandora Confirms Third-Party Data Breach, Warns Customers About Phishing
Pandora Confirms Third-Party Data Breach, Warns Customers About Phishing Pandora, the world-famous Danish jewelry brand, has confirmed it was the target of a cyberattack that compromised customer data via[…]
Attackers Breach Microsoft 365 Using Fake OAuth Apps — Here’s What You Need to Know
⚠️ Attackers Breach Microsoft 365 Using Fake OAuth Apps — Here’s What You Need to Know Cybercriminals have evolved once again. A newly uncovered attack wave is leveraging fake[…]

Kick off your Azure Automation Journey!
Automate Your Azure Like a Pro: Create an Automation Account + Scheduled Runbook Automation in Azure isn’t just a luxury — it’s a superpower. Whether you’re managing resources, rotating[…]

Step-by-Step – Create VNet Peering in Azure (Securely)
🔄 What Is VNet Peering? VNet Peering enables private, high-speed communication between two virtual networks (VNets) in Azure—across the same region or even globally. It’s like running a fiber[…]

Step-by-Step – Create a Secure Azure VNet
Step-by-Step – Create a Secure Azure VNet 🧱 What is a VNet? A Virtual Network (VNet) is Azure’s foundational building block for securely connecting your VMs, services, and workloads.[…]
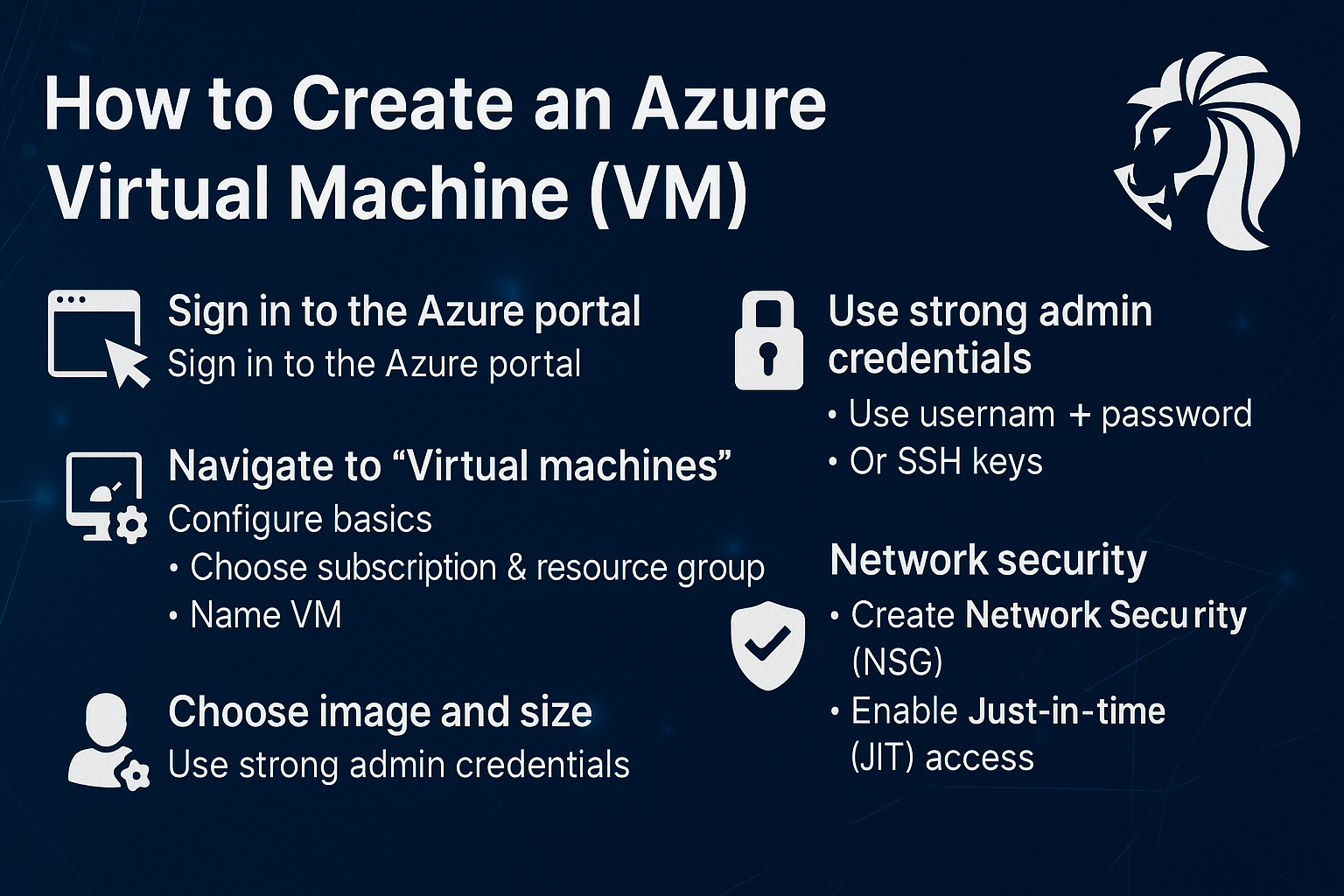
How to Create a Virtual Machine in Microsoft Azure
Deploying a Virtual Machine (VM) in Azure is one of the first tasks in cloud adoption—and it can be done in minutes. But what sets professionals apart is how[…]
